AWS Virtual Private Cloud (VPC) Demystified: A Theoretical Perspective
A Comprehensive Guide to Understanding VPC Concepts and Configuration
VPC — Virtual Private Cloud
A VPC is a virtual network in the cloud, akin to creating a private network in the cloud. Within a VPC, users can create and manage resources like servers, databases, and storage. VPCs are completely isolated from other networks, ensuring the security of resources within the VPC.
https://docs.aws.amazon.com/vpc/latest/userguide/vpc-example-private-subnets-nat.html
VPC Components:
CIDR Blocks:
VPCs can be defined using CIDR (Classless Inter-Domain Routing) blocks, which is a range of IP addresses belonging to the VPC. This CIDR determines the IP address range for the VPC.
CIDR ranges*:
192.168.0.0/24 -> allows 256 ip address
split 192.168.0.0 as*four blocks,*
192 | 168 | 0 | 0
11000000 | 10101000 | 00000000 | 00000000.
Each block has 8 bits, Totally it has 32 bits.
Out of 32 bits, 24 bits are allocated for network portion and 8 bits are allocated for host portion.
2 ^ 8 = 256 ip address.If VPC requires more range of IP address, We use 192.168.0.0/16–>65536*
i.e., 2 ^ 16–65536 Ip address.
Subnets:
Subnets are ranges of IP addresses within the VPC.
They are segments of the VPC that allow for the management of resources and control over the routing of traffic in the VPC.
Resources can be deployed into subnets, and CIDR blocks can be used to define subnets.
Subnet Types:
- Public Subnet: Public subnets in a VPC communicate directly with the internet.
- Private Subnet: A private subnet in an AWS VPC is a subnet that does not have direct access to the internet. Resources deployed in a private subnet cannot send outbound traffic directly to the internet or receive inbound traffic initiated from the internet. To enable outbound internet access for resources, a NAT gateway can be used to mask the IP address of the resources that require internet access. Private subnets have resources like servers, databases, and storage.
Routing:
A routing table defines how traffic is routed within the VPC.
Internet Gateway:
An internet gateway allows the VPC to communicate directly with the internet.
VPC Security:
Security in AWS is a shared responsibility. VPC security includes Security Groups and Network ACLs (NACLs).
Security Group:
A security group provides instance-level security for resources. By default, all ports in a security group are blocked, and specific ports or IP addresses must be allowed for access.
There are two types of traffic:
- Inbound Traffic: SG blocks all incoming traffic by default. Specific ports or IPs need to be allowed for access.
- Outbound Traffic: SG allows all outbound traffic by default. Specific ports or IPs can be blocked in outbound traffic.
Network ACL:
Network Access Control List (NACL) provides security at the subnet level. In NACLs, specific rules are defined to allow or deny inbound and outbound traffic. Rules are evaluated starting with the lowest numbered rule, and as soon as a rule matches traffic, it’s applied, regardless of any higher-numbered rule that might contradict it.
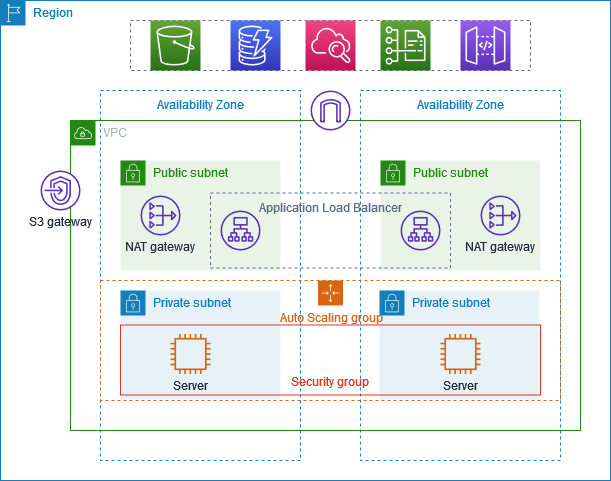
Overview of VPC:
Our VPC setup includes two availability zones, each with one public subnet and one private subnet.
The public subnet includes a NAT gateway and an Application Load Balancer (ALB).
The private subnet includes servers and an Auto Scaling group.
The Auto Scaling group dynamically adjusts the number of servers (EC2 instances) based on incoming traffic.
Each EC2 instance has a security group that controls access.
An internet gateway is used for requests passing through.
Working:
For example, if IP 172.0.0.2:6000 wants to access IP 172.1.1.0.2323 in the private subnet of our VPC:
1. The request passes through the Internet Gateway to the public subnet.
2. From the public subnet, the request is routed to the respective private subnet using the routing table.
3. NACL in the subnet allows/denies the request based on the port/IP of the request.
4. Once the request passes through the NACL, the security group verifies the request (if both NACL and security group are used), and the request is allowed to access the resource.
Private Subnet Accessing Internet:
When a private subnet tries to access the internet, its IP should not be visible to the internet. Hence, a NAT gateway is used to mask the address of the private subnet, and the request is transferred to the internet.
CONCLUSION :
In Conclusion, VPC is the isolated space where you can launch resources in the network. VPC uses various components like subnets, servers, route tables to manage the resources.
